The Paranoid Mac Owner's Guide to Defeating Remote Snooping & Evil Maid Attacks « Null Byte :: WonderHowTo

What is an Evil Maid attack and how is it different from Evil Twin attack? | Cyware Alerts - Hacker News
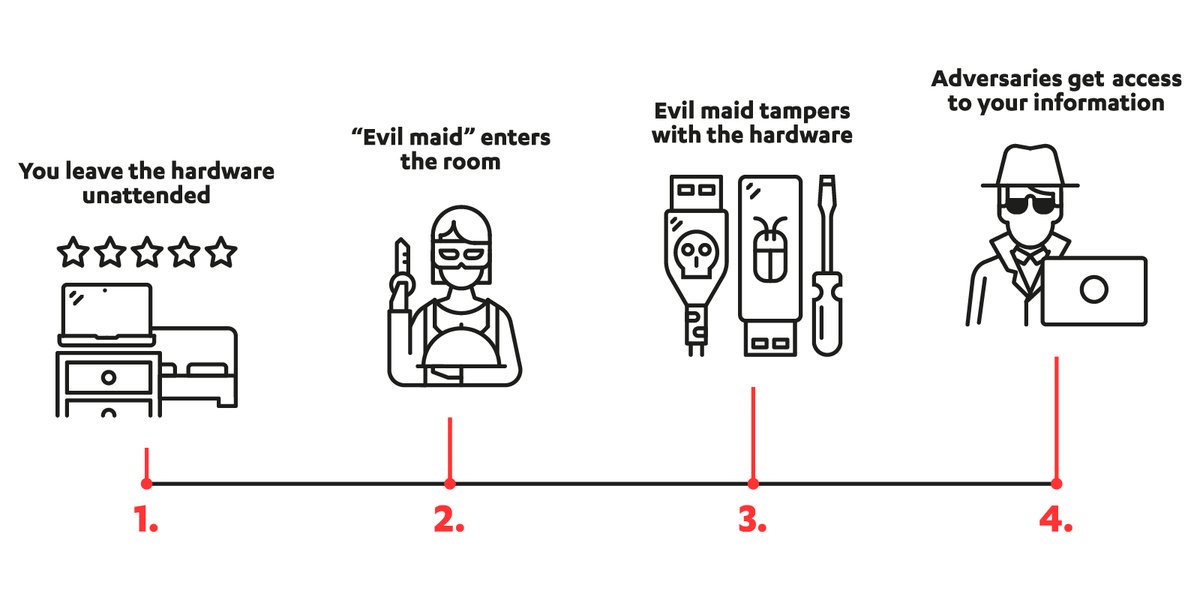
تويتر \ WithSecure™ على تويتر: "@nxsolle Attackers manipulate the firmware settings… https://t.co/59JCAD5Ph6"

Evil Maid Attack Takes Your PC To The Cleaners With Sub-4 Minute Backdoor Firmware Install | HotHardware